In the vast landscape of cybersecurity, the term “spoofing” holds a prominent place, representing a technique employed by malicious actors to deceive systems and users. This blog aims to shed light on the definition, meaning, and inner workings of spoofing, unraveling the complexities that surround this cybersecurity threat. Defining Spoofing: Spoofing, in the realm of cybersecurity, refers to the act of falsifying data or information to trick systems, users, or networks into believing that the source of the information is legitimate. This deceptive practice is often utilized by cybercriminals to gain unauthorized access, deliver malware, or execute other malicious activities. Types of Spoofing: IP Spoofing: Definition: IP Spoofing involves manipulating the source IP address in a network packet to conceal the identity of the sender or impersonate a trusted entity. How it works: Cybercriminals modify the source IP address in packet headers, making it appear as if the data is coming from a legitimate source. Email Spoofing: Definition: Email Spoofing occurs when an attacker sends emails with a forged sender address, making it appear as if the email is from a trustworthy source. How it works: By manipulating email headers, cybercriminals deceive recipients into believing that the message is legitimate, leading to potential phishing attacks or the spread of malware. DNS Spoofing: Definition: DNS Spoofing involves corrupting the Domain Name System (DNS) to redirect users to malicious websites. How it works: Attackers manipulate DNS records, associating legitimate domain names with incorrect IP addresses, diverting users to fraudulent sites. Caller ID Spoofing: Definition: Caller ID Spoofing occurs when a caller manipulates the displayed phone number to disguise their identity. How it works: Cybercriminals use Voice over Internet Protocol (VoIP) technology to alter the calling number, tricking recipients into answering potentially harmful calls. Implications of Spoofing: The repercussions of spoofing attacks can be severe, ranging from financial losses to compromising sensitive data and damaging an organization’s reputation. Here are some potential consequences: Unauthorized Access: Spoofing can lead to unauthorized access to networks or systems, enabling attackers to extract sensitive information or disrupt operations. Phishing Attacks: Email spoofing often serves as a precursor to phishing attacks, tricking users into divulging confidential information or downloading malicious attachments. Data Tampering: Spoofing can result in the alteration of data, leading to misinformation, compromised integrity, and potential legal consequences. Understanding the intricacies of spoofing is crucial for individuals and organizations to bolster their cybersecurity defenses. Implementing robust security measures, staying vigilant against phishing attempts, and regularly updating systems are key steps in mitigating the risks associated with spoofing. As technology advances, so do the tactics of cybercriminals, making it imperative for users to stay informed and proactive in safeguarding their digital assets against these deceptive practices. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
In an ever-evolving regulatory landscape, businesses must prioritize compliance to mitigate risks, build trust, and ensure long-term success. Strengthening compliance involves adopting a proactive approach, integrating compliance into the organizational culture, and staying abreast of regulatory changes. Explore key steps that businesses can take to fortify their compliance efforts and navigate the complex regulatory environment. Conduct a Comprehensive Risk Assessment: Before developing or enhancing a compliance program, it’s crucial to conduct a thorough risk assessment. Identify and evaluate potential risks associated with your industry, operations, and geographic locations. This assessment provides a foundation for designing targeted compliance measures and allocating resources effectively. Establish a Robust Compliance Framework: A well-defined compliance framework serves as the backbone of your compliance program. It should include policies, procedures, and controls that align with applicable laws and regulations. Ensure that the framework is tailored to your organization’s size, industry, and specific risk profile. Implement Regular Training and Awareness Programs: Employees are the first line of defense against compliance risks. Regular training programs on relevant laws, industry regulations, and internal policies are essential. Promote a culture of compliance by fostering awareness and ensuring that employees understand their roles in maintaining regulatory adherence. Utilize Technology for Compliance Monitoring: Leverage technology solutions to streamline compliance monitoring and reporting processes. Automated systems can help in tracking regulatory changes, monitoring internal controls, and generating real-time compliance reports. This not only enhances efficiency but also provides a more accurate and timely assessment of compliance status. Establish Clear Communication Channels: Open and transparent communication channels are crucial for addressing compliance concerns. Establish a mechanism for employees to report potential violations without fear of retaliation. Encourage a culture where employees feel comfortable seeking guidance on compliance-related matters. Regularly Update Policies and Procedures: Laws and regulations are dynamic, and compliance frameworks must adapt accordingly. Regularly review and update policies and procedures to reflect changes in the regulatory environment. This ensures that your organization remains agile and compliant in the face of evolving legal requirements. Conduct Internal Audits and Monitoring: Internal audits are instrumental in evaluating the effectiveness of your compliance program. Conduct regular assessments to identify areas for improvement and address any compliance gaps promptly. Monitoring internal controls is an ongoing process that helps prevent and detect potential compliance issues. Collaborate with Legal Experts: Establish strong collaborations with legal experts who specialize in your industry. This partnership can provide valuable insights into emerging regulatory trends, legal interpretations, and best practices. Legal counsel can guide your organization in navigating complex compliance challenges. Stay Informed about Regulatory Changes: Regulatory landscapes are constantly evolving. Regularly monitor changes in laws and regulations relevant to your industry. Subscribe to regulatory updates, participate in industry forums, and engage with regulatory bodies to stay informed about impending changes that may impact your business. Foster a Culture of Ethics and Integrity: Beyond mere compliance, fostering a culture of ethics and integrity is paramount. Emphasize the importance of ethical behavior at all levels of the organization. This not only strengthens your compliance posture but also contributes to building a positive corporate reputation. Strengthening compliance is an ongoing process that requires commitment, adaptability, and a proactive mindset. By following these key steps, businesses can create a resilient compliance framework that not only meets regulatory requirements but also contributes to long-term success and sustainability. Remember, compliance is not just a checkbox—it’s a fundamental aspect of responsible and ethical business practices. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
In our digital world, we have multiple devices and accounts to our name. This increases the risk of breaches and gives malicious actors access to sensitive information and account credentials. Biometric authentication revolutionizes how we verify ourselves when opening any secure account or device. This guide uncovers the benefits of biometric authentication and how it can help protect your business. What Is Biometric Authentication? Think of how you must verify your identity when logging into any account. These mostly include: Answering security questions Entering passwords and PINs Confirming identity with a one-time verification passcode These outdated measures leave you susceptible to security breaches since the information is only sometimes iron-clad. Biometric authentication offers a much more secure way of logging in since it verifies users through unique physical characteristics. Using facial or fingerprint recognition is a highly secure method of ensuring only the rightful user can access an account. Behavioral biometric authentication adds another layer of security. Devices can identify key characteristics that match someone using knowledge based on their activity, such as swiping or scrolling patterns. Benefits of Biometric Authentication for Businesses Why are experts recommending this technology for business leaders? Adjusting authentication measures can have a tremendous impact on how businesses operate as well as their reputation. Take a look at some of the biggest benefits biometric authentication offers below. Reduced Cyber Threat Risk By doing away with vulnerable passwords and security question answers, your company can minimize the threat of security breaches. Threat actors will have a harder time trying to infiltrate accounts within your network if you utilize unique physical features as the primary form of user verification. Safeguarding accounts with either fingerprint matching or facial recognition scans makes you less prone to experiencing identity theft, ransomware, and other threats. Improved Customer Loyalty Say you operate a major financial institution and have many customers moving their funds elsewhere due to security concerns regarding your mobile banking app. By implementing biometric authentication to your mobile app, customers now have a safe and efficient way to access and monitor their accounts. This is a great way to instill a customer’s confidence in your brand and increase loyalty. Satisfied customers are a boon to your business, allowing you to expand outreach and operations whenever they recommend others to use your services. Money Savings Having a large, loyal customer base that recommends your business to others means you can save on customer acquisition costs. In addition, the lower risk of cyber threats gives you a chance to cut back on expensive cybersecurity programs and software. Just by adding biometric technology, your business can see savings stack up. Boost Your Business Security With Biometric Technology With so many benefits of biometric authentication, why not take advantage of this technology within your business? You can easily reduce the risk of device hacking with one-of-a-kind biometric identifiers. Consider implementing this technology into your daily life to make sure that only sanctioned users can log in to important devices and accounts. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
As a modern business owner, you’re well aware of all the ways technology benefits your business while also putting it at risk. If you use Google Chrome as your browser of choice, you should be aware of the latest Google Chrome update malware scam. Keep reading to learn everything you need to know about this attack campaign, how to determine whether you have a compromised website, and how to protect yourself against security risks. What Is Update Malware? Update malware is the term for any line of malicious code cyber attacks embedded within an update to your computer system, website, or web browser. When you download the update, the code you install puts hidden files on your computer that grant the attacker access to your private information or critical computer systems. How the Scam Works Cybersecurity experts have identified at least four different fake “update your browser” campaigns that can trick you into installing malware on your device. This scam was first detected in February 2023 and since then has evolved to provide the attackers with multiple ways to invade your system. The first way they accomplish this is by gaining access to legitimate websites, which they do in various ways. Once they have access to the website, they modify it to display a pop-up to every user who visits the website. The pop-up informs the user their browser is out of date and requires them to update to the newest browser version if they want to view the website’s content. Once users click on the pop-up, they’ve compromised their computers. Determining Whether You Have Malware You can determine whether you’re a victim of the Google Chrome update error by looking for the following file types: SocGholish NETSupport RAT Lumma Redline Raccoon v2 These files make you vulnerable to more severe cyberattacks like identity theft. You can use a virus scanner to find these files, or your IT services team can find them easily. How To Protect Yourself From Google Chrome Update Malware How can you protect your business from malware? First, educate your users on the best practices for avoiding malware, which include: Avoid phishing scams by never clicking on a link to an unknown site or from an unknown sender. Learn to identify typical phishing attack behavior, such as generic greetings, asking for financial information, or promotional offers that are too good to be true. Use multi-factor authentication on all devices. Invest in high-quality anti-virus protection software. Regularly back up your data to a secure location. Use strong passwords and change them regularly. You can also protect yourself from the Google Chrome update malware scam by practicing good “cyber hygiene” and learning how developers push out updates. For example, Chrome will never prompt you to update the browser through a pop-up. You should only update the browser through Chrome’s settings, which notify you of new updates in the upper right-hand corner of the browser. You should also enable automatic updates. This allows your computer or browser to download safe and secure updates without requiring you to click on anything. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Data breaches and security vulnerabilities are rising, and not everyone is safe from emerging threats. The NSA and CISA report that many businesses need to follow the best practices. Discover some of the most common business security mistakes and how to stay safe in this helpful guide. Default Login Credentials Pose the Biggest Threat Nearly every application or business program executives use has standard default login credentials. Experts recommend only using these factory settings when you first set everything up. As soon as the programs are ready for use, it’s best to change the account’s credentials. This way, hackers have a lower chance of infiltrating your account. Creating strong passwords for all your accounts is essential to boosting network security, yet reports find that many IT professionals continue to use factory settings. Harmful Business Security Mistakes While using default credentials on applications and software is the most prevalent issue, CISA and the NSA note a few other security mistakes businesses regularly make. Experts recommend business owners make correcting these issues a top priority. Separating User and Admin Privileges Does your IT department grant anyone access to programs as an admin? Doing so can create big problems if they uncover malicious activity. It’s hard to pinpoint where the problem originates if every user has advanced privileges. Hackers can infiltrate the account and have unauthorized access to important data and information. Therefore, it’s critical to only give admin privileges when necessary and give all other users limited access to accounts. Poor Network Monitoring Experts point to a few ways companies need to monitor their networks sufficiently. These include failing to properly set up sensors to collect traffic and end-host logs. Stepping up in this area is essential to improve your business infrastructure and keep your network secure from threats. Importance of Cybersecurity Measures Some business leaders don’t realize they’re dropping the ball on security measures until too late. Falling victim to any cyber attack comes with significant problems, including: Loss of integrity and customer trust Data breaches Financial loss Business interruptions To avoid these costly consequences, technology professionals urge every business owner to emphasize the importance of cybersecurity in their workplace. Making IT staff regularly educate employees on the best practices sets up the entire organization for success. In addition, it’s vital to keep an eye out for emerging threats and take proactive measures. This may include downloading software updates after vulnerability exposure or adjusting security practices at the recommendation of agencies like CISA and the NSA. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
You can only make an online account with a username and password. The password manager tool in your web browser has an autocomplete function that quickly fills in your password field. This is handy but also makes you vulnerable to dangerous cyber activity. Learn why cybersecurity experts warn against using autocomplete for passwords and learn tips for protecting your account credentials. Password Manager Programs Are Useful — But Turn Off Autocomplete Websites that need a password to access the autocomplete feature use an embedded password manager program to do this. These apps make it easy to autofill passwords with just one click instead of having to remember a string of letters and numbers. Hackers who infiltrate a vulnerable website can set up an invisible login form. By using the autofill feature, your login credentials will appear on the hidden form, giving hackers your information without you even knowing. Password management programs are worthwhile for many business websites. However, using autocomplete for passwords makes you vulnerable to malicious hackers. Turn off this function on your password manager for heightened cybersecurity. Most Internet Users Lack Password Diversity Think about how many tools and apps your business uses that are online. Each program needs a different login so your staff can access the account. But in the U.S., only 20% of Internet users make different passwords for each account. Hackers can easily get into most of your accounts if you use the same password on different sites. When that happens, most of your private information is no longer safe. Ad Networks Target Your Login Form Fields Avoiding hackers is the main reason to avoid using autocomplete for passwords. However, there’s another group of Internet users you want protection from. Ad networks use the same techniques as hackers to get your information, but instead of doing something bad, they use it to send you more relevant ads. If you type out text instead of using autocomplete, advertisers can’t use tracking tools to see your email address. Even though ad networks say they don’t store your password, there is always a chance that your information could be used in a dangerous way if it gets into the wrong hands. Turn Off Autocomplete for Passwords to Protect Your Information Experts say you don’t have to stop using a password manager in your business, but you should turn off automatic password inputs. Changing a few settings in your computer browser is all it takes. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Modern technology makes it much easier to operate a business. However, it can also cause major issues if you somehow lose access to critical data within your network. That’s why having a backup solution is important so all your data remains safe and readily accessible. Discover the crucial role of data backup and recovery in this helpful guide. Why Data Backup and Recovery Is Important Say a major storm passes through the area and your company’s building floods. The flood ruins all of your computer hardware, and you cannot access necessary data from another location. You can do nothing to stop natural disasters, but you can minimize the business impacts. Backing up all your data securely means you can resume business operations even if you suddenly need to work remotely. Data backup and recovery are also necessary to protect your business from human error. Say you accidentally delete an important file that is a key part of your latest project—having no backup copy available forces you to delay your project and hurts productivity. Performing frequent backups makes recovery times much faster so you can continue routine business operations. Your productivity won’t suffer if you can easily access an external drive or cloud server that contains your files and data. How Often Should You Perform Data Backups? Now that you understand the essential role of data backup and recovery, let’s discuss how often you need to back up your data. Technology experts urge every business leader to perform backups frequently. The longer you go without backing up your data, the longer your recovery time will be if the unexpected happens. Overcoming a natural disaster, accidental deletion, or system failure will be much simpler when you know you can easily access your data. For this reason, professionals recommend performing backups either daily or weekly. You can customize your schedule depending on how frequently your critical data changes. Data Backups Safeguard Your Business From Cyber Attacks One of the most important reasons you need to back up all sensitive data is to protect your business from malicious activity. Cybercriminals can perform data breaches that significantly affect companies and their clients. It’s much easier to mitigate the damage when you have a backup copy of files to deploy. Business leaders and their employees should habitually back up important data if a cyberattack occurs. Other measures that experts recommend include: Using strong encryption methods Regularly updating software programs Using multi-factor authentication to prevent hackers from gaining unauthorized access Teaching employees the best cybersecurity practices By protecting your data, you can avoid the dangers of cyberattacks. Protect Your Business Knowing the role of data backup and recovery can help you safeguard your business from physical and virtual threats. Counting on backup services can give you peace of mind regarding involuntary data loss. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
A new phishing campaign is making the rounds in an attempt for hackers to obtain sensitive information from vulnerable users. This campaign, first uncovered by tech researchers at Checkpoint, targets the popular cloud storage platform Dropbox. Learn more about the cybersecurity threat and how you can stay safe. Dangers of Phishing Hackers create ways to trick users into giving out their personal information, such as with deceptive emails or links to fake websites. They use messaging that claims a user needs to act urgently and provide sensitive data, such as credit card numbers or banking information. Once the hackers have this data, they can do with it as they please and wreak havoc on unsuspecting people. The dangers of phishing extend to business owners, their employees, and beyond. Victims must deal with the following issues: Financial loss or identity theft Violation of safety Lack of trust online How the Dropbox Phishing Campaign Works This clever campaign has several parts to it. Let’s review how hackers execute their plans step-by-step. Hackers Host a Document on Dropbox The plan begins with unknown bad actors creating a Dropbox account. They host a benign document that looks like a file from OneDrive and send phishing emails to users. Dropbox users will see a button that says “view document.” If they click, it leads them to malicious links. Hackers can implement the next phase after users end up on this site. Distribution Phase A key part of this Dropbox phishing campaign is getting users to a malicious site to harvest their credentials. Once someone ends up on this page, their information is given to cybercriminals who can use it against them. If you fall for the first part of the plan and have hackers stealing your credentials, it can be challenging to feel secure online again. Why This Attack Is Hard to Recognize Checkpoint reports that thousands of users have fallen victim to this attack. It’s particularly challenging to avoid since hackers use Dropbox’s system to share files and notify other users via email. Since the email comes from a reputable source, hackers can bypass any email scam filters or other protective measures you set up. This ultimately makes you more likely to open malicious links. The best way to keep your information safe from bad actors is to always be on guard. Refrain from assuming every email you receive is secure; report it immediately if something seems a little off. Experts recommend that business owners take the time to educate their employees on safe practices and report any suspicious email to an IT professional. Protect Your Business from Threats Every phishing campaign is different, but the threat remains the same. Keep your business safe from hackers by always staying alert and tracking widespread online campaigns. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
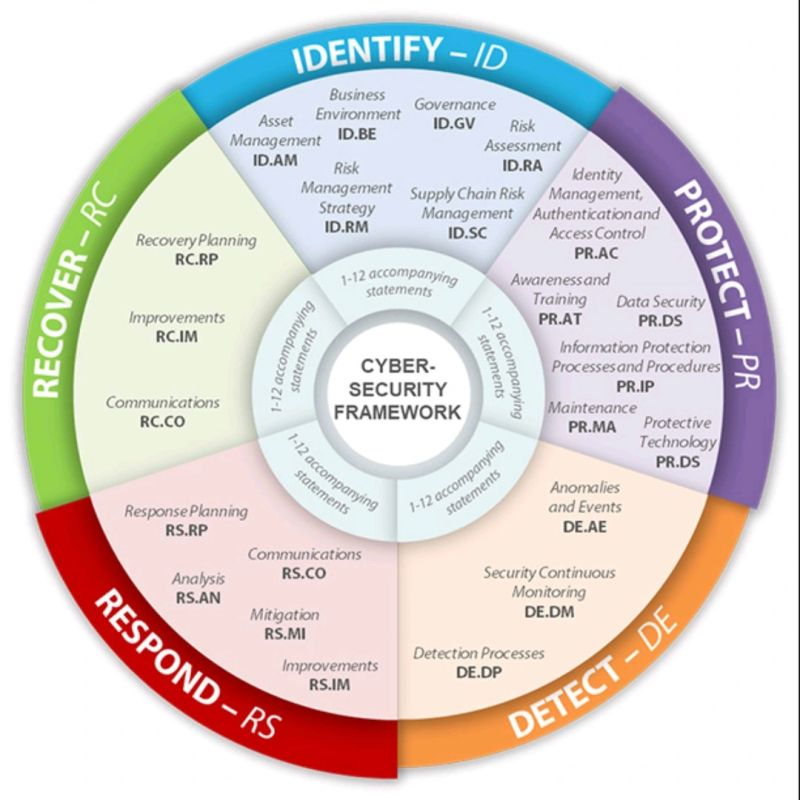
The NIST Cybersecurity Framework (CSF) stands as a cornerstone in the ongoing battle to secure our digital landscape. In today’s interconnected and data-centric world, safeguarding sensitive information and shielding organizations from cyber threats is paramount. At its core, the NIST CSF offers a comprehensive and adaptable approach to managing cybersecurity risks. It provides essential principles, best practices, and guidelines that empower organizations of all sizes and sectors to safeguard critical assets and bolster their overall cybersecurity readiness. Let’s delve into the framework’s fundamental components: 1️⃣ Identify: This initial stage revolves around recognizing an organization’s most valuable assets, such as customer data, intellectual property, and financial records. By understanding what needs protection, organizations can strategically prioritize their security efforts. 2️⃣ Protect: In this phase, implementing safeguards, preventive measures, and security controls is crucial. Activities like access control, employee awareness training, and encryption are key components, helping mitigate potential risks and vulnerabilities effectively. 3️⃣ Detect: Given the ever-evolving nature of cyber threats, it’s vital to establish mechanisms for promptly identifying and detecting potential incidents. Investments in advanced monitoring systems, boundary protection, and intrusion detection tools empower organizations to respond swiftly and effectively. 4️⃣ Respond: In the unfortunate event of an incident, having an organized and well-defined response plan is critical. This stage involves establishing communication protocols, incident reporting guidelines, and threat mitigation strategies to minimize damages and reduce downtime. 5️⃣ Recover: Following an incident, the focus shifts to restoring an organization’s systems, data, and processes to normalcy. Incorporating recovery strategies, backups, and continuous monitoring aids in bouncing back stronger and gleaning valuable insights from the experience. By embracing the NIST Cybersecurity Framework, organizations can: ✅ Foster Common Language: The framework enables the creation of a shared vocabulary around cybersecurity, fostering better collaboration between IT departments and executives. ✅ Assess and Improve: Organizations can assess their current security posture, identifying areas for enhancement and improvement. ✅ Enhance Communication: Clear communication of security efforts to clients, partners, and stakeholders builds trust and credibility. ✅ Strategic Alignment: The framework helps organizations prioritize resources, focus investments, and align cybersecurity initiatives with overall business objectives. However, it’s essential to recognize that cybersecurity is not a one-time event. Regular updates, reviews, and continuous improvement are imperative to stay ahead of emerging threats and maintain a robust security posture. Stay vigilant, stay updated, and stay secure. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
In the past, companies had to manage extensive computer networks on their own, purchasing servers and networking appliances and allocating physical space for data centers. However, the advent of cloud computing has transformed this landscape significantly. Today, companies can delegate most of their operations to the cloud, retaining only their LANs within their premises. The hybrid approach, where essential parts of the infrastructure remain on-site while other components migrate to the cloud, has gained popularity. Cloud service providers like AWS, Google Cloud, and Microsoft Azure have played a pivotal role in this shift, offering remarkable agility and flexibility. Cloud computing allows rapid scalability. If a company needs to double its data capacity, a simple adjustment in the subscription plan and some basic configurations can achieve this. Despite these advantages, effective management of cloud assets and cybersecurity remains crucial. Understanding Cloud Asset Management (CAM): When a company transitions its IT assets to cloud networks, these assets, such as hardware, software, and networking entities, become cloud assets. However, ensuring the seamless functioning and security of these cloud-hosted assets require expertise in Cloud Asset Management (CAM). CAM involves meticulous tracking of every aspect of a company’s cloud estate, encompassing maintenance, compliance, upgrading, and disposal of cloud assets. It’s imperative to be aware of the security features offered by cloud service providers and not overlook available security tools, as instances of underutilization have occurred. Challenges and Best Practices in CAM: Visibility into cloud assets presents a unique challenge. You can’t secure what you can’t see, making monitoring a critical practice. Networking monitoring tools become essential for ensuring that cloud providers adhere to Service Level Agreements (SLAs). Monitoring bandwidth and uptime guarantees the reliability of cloud assets, especially when numerous users depend on them simultaneously. Redundancy and automation are key allies in maintaining high uptime. Minimizing single points of failure, having data backups, and employing redundant servers enhance reliability. Automation not only reduces human error but also optimizes efficiency, particularly in repetitive cloud management tasks. A robust risk management plan is vital. Identify potential risks such as natural disasters, cyber attacks, and power outages. Develop specific procedures for each risk and ensure employees are trained accordingly. Security Assurance and Compliance: Critical security measures should be continuously monitored through actionable assessments. Automated systems can rectify vulnerabilities without human intervention, ensuring no security gaps are left unaddressed. Non-compliant cloud resources must be promptly shifted back into compliance, meeting the legal requirements of cloud technology. Incorporating my perspective, effective CAM not only provides security but also offers a strategic advantage. Understanding the nuances of cloud asset management empowers businesses to optimize their cloud usage, control costs, and ensure a seamless migration process. Moreover, it fosters a proactive approach, enabling companies to stay ahead of potential risks and leverage cloud resources to their fullest potential. In conclusion, CAM is pivotal for businesses embracing cloud computing. Remember, your cloud assets deserve the same attention as those behind your firewall. Stay vigilant, stay secure, and leverage the full potential of cloud services for your organization’s growth. Citation: Meena R., Cloud, Luminis India, October 16, 2023, https://luminisindia.com Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter