There are several ways a business can enhance and optimize its operations. A customer relationship management (CRM) system is one technology that may considerably assist your organization. A CRM system is software that helps businesses manage and optimize customer interactions and data across the customer lifecycle, from lead creation to nurturing. There are several key advantages to using a CRM system for lead generation and nurturing. First and foremost, a CRM system allows you to centralize and organize your customer data in one place. This includes contact information, communication history, and any notes or comments about the customer. Having this information easily accessible allows you to better understand your customers’ needs and preferences, as well as effectively communicate with them. A CRM system helps you concentrate and manage all your client data in one location. Contact information, communication history, and any notes or remarks regarding the consumer are all included. Having this information available enables you to understand better your clients’ requirements and preferences, as well as effectively communicate with them. In addition to improving sales and marketing efficiency, a CRM system can also help increase customer loyalty. By managing customer interactions and communication through a CRM, you can provide a better overall customer experience. This can increase customer retention and positive word-of-mouth marketing for your business. The advantages of a CRM system don’t end there. Your sales process may be streamlined and optimized with a CRM. For instance, you may use a CRM to track a prospect’s journey through the sales funnel and see any bottlenecks or areas where businesses can improve. Companies may also use a CRM to manage their sales team, monitor sales performance, and assign tasks. A CRM system is a valuable tool for small IT companies aiming to enhance their lead generation and nurturing efforts. In addition, a CRM may help you expand your business and create lasting relationships with your clients by improving consumer insights, sales, marketing efficiency, and customer loyalty.
As a business owner, you realize the necessity of being competitive in a rapidly evolving industry. One method is to use technology to simplify your operations. The proper strategies and tools can boost productivity, cut expenses, and help you provide better customer service. A few strategies for achieving these objectives are: Automate repetitive tasks: Many IT activities, such as server configuration and software installation, are repetitive and time-consuming. These tasks may be handled by automation systems with little involvement from you, freeing up your time to concentrate on other crucial work. Scripts, macros, and integrations are just a few of the various automation solutions that may be tailored to your company’s needs. Use project management software: Managing a small IT firm requires managing several clients and projects simultaneously. You may access project management software from any device with an internet connection to keep track of tasks, deadlines, and resources. This will assist you in staying organized and fulfilling your obligations while also providing better teamwork and communication. Adopt cloud computing: There are several advantages to moving your company’s data and apps to the cloud. Thanks to cloud computing, you may access your data from any device with an internet connection, which can lessen the requirement for on-premises infrastructure and software. This can reduce the cost of maintenance and updates while also making it simpler to scale your business as it grows. By implementing these technologies, you can streamline your business’s operations and improve its efficiency. Automating repetitive tasks and using project management software can save you time and reduce the risk of mistakes. Another advantage is that adopting cloud computing can save you money and make it easier to scale your business. By taking advantage of these tools, you can better serve your clients and stay competitive in a rapidly changing industry.

Project management software is quickly becoming a necessity for businesses of all sizes. It has the potential to increase efficiency and productivity by streamlining project management tasks and reducing manual processes. These tools are integral in helping businesses manage their projects, save time, and increase profits. With a wide variety of features and customizable options, project management software can be tailored to fit almost any need, from large-scale corporations to small businesses. Whether increasing productivity and efficiency or saving money and time, when used properly, project management software can be an excellent tool for businesses to manage their projects. Project management software is an excellent tool for businesses to manage their various projects seamlessly. This software can include tools such as expense tracking and streamlining other organizational goods. Having all the project-related information in one place means team members don’t need to search multiple places for information. It can also assist in creating a more organized project structure. Project management software can be invaluable when managing complex projects or working with remote teams. Other project management software can be beneficial for streamlining the project management process. These tools allow users to track the progress of a project and keep an eye on expenses as well as team members working on a project. As a result, businesses can better plan for any potential obstacles with a project and be proactive in solving them before they occur. This increases productivity and ensures that a project runs smoothly and on budget. Furthermore, it allows project managers to keep employees informed and on task, ensuring that everyone follows the set timeline and stays on the same page. These kinds of software can make managing a project simpler and less stressful. Project management software can increase collaboration, speed up completion times, and reduce stress; however, it can also have damaging effects if not properly implemented. Setting realistic standards for reaching goals is essential, as the software will only be able to function if goals are manageable and specific. Ultimately, project management software can help businesses increase their success and achieve their goals.
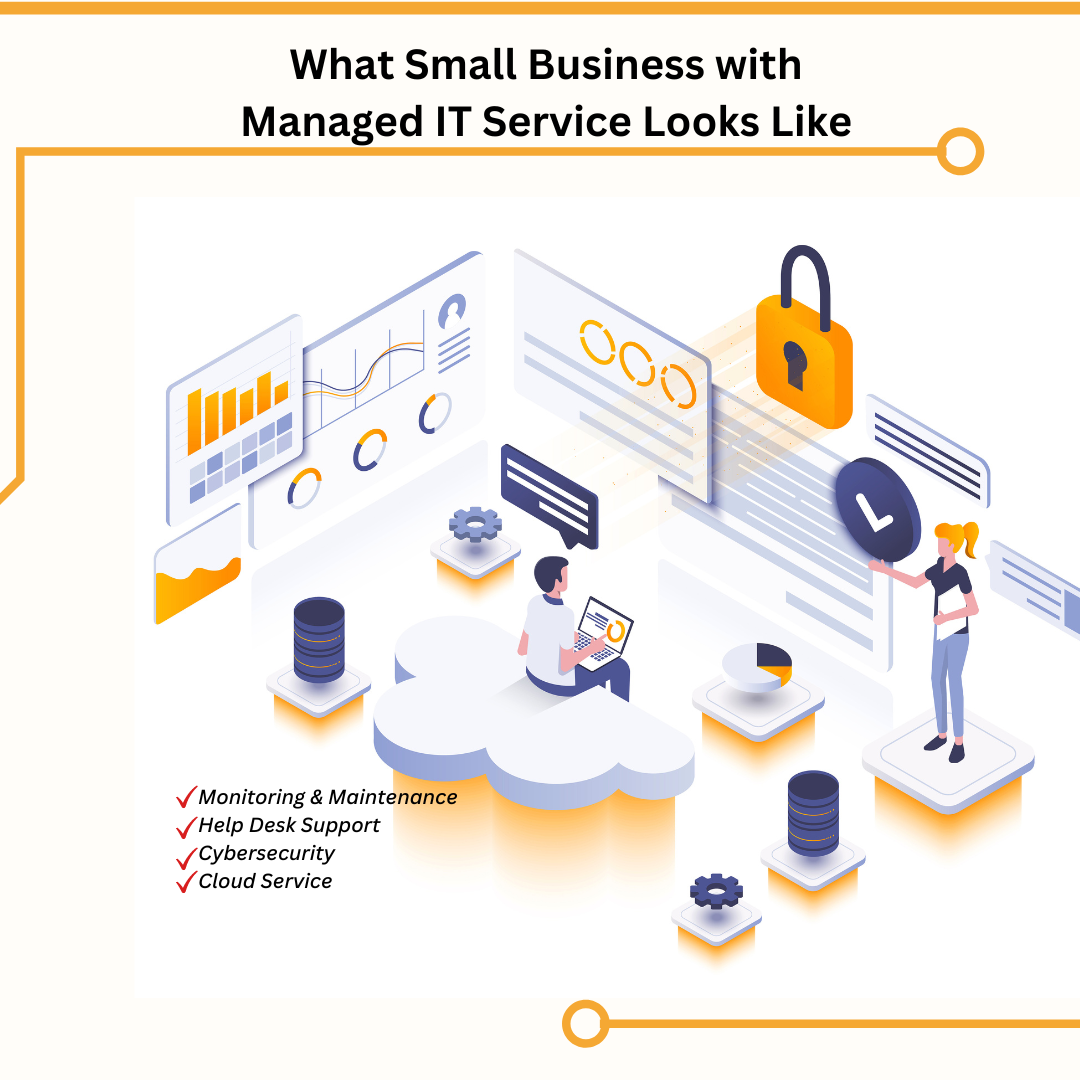
As a small business owner, your business may face various challenges regarding IT support, such as limited resources or lack of experience. This is why it’s essential to have reliable IT systems in place, as they can be valuable allies in solving these challenges. Small businesses may outsource their IT support needs to a team of professionals thanks to managed IT services. These experts have the knowledge and resources necessary to offer complete IT assistance. In addition, by outsourcing to an IT provider, small companies have access to the knowledge and experience of a team of specialists who can help them manage complex challenges. Managed IT services are available to small businesses in several forms. Some of these services include: Monitoring and maintenance – Managed IT service providers can monitor your business devices around the clock, looking for potential issues and performing regular maintenance to keep them running smoothly. Help desk support – Managed IT service providers offer help desk support, providing small businesses with a team of professionals to answer questions and assist when issues arise. Cybersecurity – Small businesses are constantly at risk of cyberattacks, and managed IT services can help protect them by providing comprehensive cybersecurity services such as security assessments, vulnerability testing, and incident response. Cloud services – Managed IT service providers can also help small businesses migrate to the cloud, providing guidance and support. One of the main advantages of working with a managed IT service provider is having access to a team of professionals without recruiting internal IT workers. Small firms that lack the funding or the capacity to hire a full-time IT team may find this to be of particular help. Small businesses can save time and money by utilizing managed IT services because they no longer need to invest in internal IT personnel or resources. Managed IT services can be a useful tool for small firms trying to get above the obstacles posed by a lack of resources and knowledge. Small company owners may obtain the expertise and experience they need to operate their IT systems successfully while saving time and money by outsourcing their IT support requirements to a team of experts.
It can be challenging for business owners to keep up with the latest technology trends and determine which ones are worth investing in. However, businesses must stay current with technology to remain competitive in today’s market. The following are the top three technology trends every business owner should be aware of: Cloud computing: Cloud computing is the delivery of computing services such as storage, processing, and networking over the internet rather than through local servers. By implementing cloud computing, businesses can reduce IT costs, increase flexibility and scalability, and improve collaboration and productivity. However, before moving to the cloud, companies should carefully assess their data security and compliance requirements. Managing IT services can help businesses adopt cloud computing and protect their data. Artificial intelligence (AI) and machine learning: With artificial intelligence (AI) and machine learning, tasks are automated, large amounts of data are analyzed, and personalized experiences are provided to customers. In addition to improving operations and increasing efficiency, AI and machine learning can help businesses reduce costs. However, companies should consider the skills and resources needed to implement and manage these technologies effectively. IT-managed services can help enterprises to implement and integrate AI and machine learning into their operations. Internet of Things (IoT): The Internet of Things refers to a network of connected devices, sensors, and systems that communicate and exchange data over the internet. The Internet of Things can help businesses automate processes, enhance efficiency, and collect valuable data insights. IoT devices can, however, be vulnerable to hacking and cyberattacks, so security is a significant concern. Managed IT services can help businesses secure their IoT devices and protect their data. Companies must stay up to date with technological advancements if they want to remain competitive and accomplish their goals. Companies that employ cutting-edge technology can benefit significantly. However, to successfully implement and manage their demands, they must carefully assess them and ensure they have the necessary resources and assistance. With managed IT services, companies can handle the adoption of new technologies and ensure they are utilized securely and compliant.
Hackers are baiting their victims with stolen financial data in a clever phishing scheme. Over 400,000 data points, including identity numbers, names, phone numbers, and payment records, are used to persuade consumers to click on a malicious link. This link downloads a potent virus called BitRAT that can steal passwords, spy on users, and install crypto mining software. In order to spread the remote access trojan known as BitRAT, the new campaign utilized confidential data taken from a bank as bait in phishing emails convincing victims to download a suspicious Excel file. BitRAT is a well-known remote access trojan (RAT) sold on dark web markets and forums used by cybercriminals. Because it costs $20 for a lifetime membership, it attracts all sorts of hackers and promotes the propagation of harmful payloads. In addition, the fact that BitRAT can be utilized in a range of activities, including phishing attacks, trojanized software, and watering hole attacks, makes it much more difficult to block. Although the hacker group responsible for the campaign is currently unknown, it is believed that they used SQL injection flaws to compromise the IT network of a Colombian cooperative bank. This is a typical method used by hackers to trick a database into producing an error message so they may discover the layout of the database. The exposed information includes, among other things, ID numbers (national resident identity), phone numbers, email addresses, customer names, income information, payment history, and residences. There are no indications that the information has been posted on any forums. However, this does not mean that consumers should not worry. The threat actors could use the obtained data to carry out phishing attacks themselves. The exfiltrated bank data file also has a macro embedded that downloads a second-stage DLL payload programmed to fetch and run BitRAT on the infected host. According to Qualys researcher Akshat Pradhan, the infected file downloads BitRAT embedded payloads from GitHub to the %temp% directory via the WinHTTP library. The GitHub repository, established in the middle of November 2022, stores encoded BitRAT loader samples, which are later decoded and launched to finish the infection chains. It’s crucial for business owners to be aware of these types of threats. Businesses can take proactive measures to protect their systems and sensitive data. Training employees to recognize and avoid suspicious emails and links and ensuring all systems are kept up-to-date with the latest security patches are just a couple of ways business owners can reduce the risk of falling victim to cyber-attacks.
As a managed IT Service provider, we understand the importance of technology in helping businesses stay competitive in the digital age. In today’s fast-paced business environment, staying up to date with the latest tools and technologies is essential for success. However, for small and medium-sized businesses, this can be a challenge. It can be difficult to stay competitive without the resources or expertise to keep up with the latest trends and developments in the tech world. That’s where managed IT services come in. By outsourcing your IT support to a managed service provider, you can ensure access to the latest tools and technologies without investing in the time and resources required to stay current. But how exactly can managed IT services help your business stay competitive? Here are just a few ways: Stay ahead of the curve: With a managed IT service provider on your side, you can be sure that you’re always using the latest tools and technologies. This can give you a competitive edge over your competitors, who may not have access to the same resources. Improve efficiency: By streamlining processes and automating tasks, managed IT services can help your business run more efficiently. This can free up time and resources that you can use to focus on other areas of your business. Enhance security: Cybersecurity is a critical concern for businesses of all sizes. Managed IT services can help you keep your data and systems secure, giving you peace of mind and helping you protect your business from potential threats. Scale up as you grow: Your IT needs will change as your business grows and evolves. Managed IT services can help you scale up and adapt to these changes, ensuring you have the resources and support you need to succeed. Managed IT services can be a valuable resource for businesses looking to stay competitive in the digital age. By outsourcing your IT support to a managed service provider, you can access the latest tools and technologies, improve efficiency, enhance security, and scale up as you grow. Whether you’re a small business owner looking to get a foothold in your industry or a larger company looking to stay ahead of the competition, managed IT services can help you succeed. A managed IT service provider is an excellent choice for your business if you want to stay competitive.
A recently discovered exploit in Log4j, an open-source logging library used by multiple services and applications across the internet, allows attackers to execute remote code on any vulnerable servers. If exploited successfully, attackers can upload and import malware onto compromised servers, rendering those servers, and any machines that may connect to them, infected. Nearly every network security system runs a daily log, a list of activities performed, of activities that occurred on said network. As you can imagine, this gives popular logging libraries, like Log4j, immense reach, leaving millions of machines and servers vulnerable to attack. In order to exploit the vulnerability, an attacker simply needs to save a specific string of characters in the log. Since logging systems save a wide variety of events, such as messages received and sent by users, this exploit is extremely easy to take advantage of and can be triggered in a variety in ways. Due to the variety of applications vulnerable to the exploit and the immense range of possible ways to deliver the attack means that firewall protection alone cannot adequately protect your machines or servers. However, there has been an update to the log4j library, aimed at mitigating the vulnerability, but it will take time to ensure all machines are properly updated to protect against this exploit. Worried about your business’s network security? Need an IT team that focuses on helping your business succeed? At Hammett Technologies, we put your online security as a top priority. We treat your network as our own, with regular maintenance and updates to keep your company’s data secure and out of the hands of criminals. Be with a team you can trust. Become a Hammett Technologies partner today and rest easy knowing your business’s network is secure!
Positive Technologies released an article on October 26, 2021 discussing the creation and development of rootkits in cyber attacks. Their research discovered that 77% of rootkits are used against government agencies. Rootkits, a dangerous type of cyber attack, are designed to intercept system calls, replace software and system processes, and may also contain keyloggers that can be used to steal your data. While this type of cyber attack is dangerous, they are far less common than other forms of malware. Due to their complex nature, the majority of rootkit attacks come from advanced persistent threats (APTs), cyber criminal groups who have the resources to create and carry out more complicated and expensive attacks. Therefore, because of the difficult in creating them, the target must be considered “high-value”. The majority of the time, the attackers using rootkits are attempting data-theft, but there are cases where the goal is strictly financial. While the majority are used against government agencies, rootkits have also been used against telecommunication companies, manufactures, and financial institutions. In addition to business, rootkits may also target specific individuals considered to be “high-ranking”. This could be political figures, military officers, and even business owners. It is important that you learn to protect yourself from these types of attacks. At Hammett Technologies we put your online security as a top priority. We treat your network as our own, with regular maintenance and updates to keep your company’s data secure. Be with a team you can trust, become a Hammett Technologies Partner today!
Artificial Intelligence (AI) is becoming a cybersecurity team’s best defense against hackers, reports suggest. Moreover, as we continue to progress with technology, the dependency on AI to help protect our personal and business technology is increasing. More and more businesses and cybersecurity companies are turning to artificial intelligence as a means of bolstering their defenses against cyber-attacks, and with ever-increasing positive results. According to Capgemini’s article, Reinventing Cybersecurity with Artificial Intelligence, artificial intelligence is becoming a necessary factor in a business cybersecurity defense. As much as 66% of cybersecurity firms believe that they would be unable to detect cyber-attacks without the assistance of their AI. As much as 75% of cybersecurity firms are beginning to test artificial intelligence. 60% believe that artificial intelligence has dramatically improved the accuracy and efficiency of cybersecurity technicians and analysists. With over half of all cybersecurity firms and businesses opting for AI for their cyber defense, artificial intelligence is not only becoming more sought after but also more dependable. With the globe becoming more dependent on technology each day, it should be no surprise that criminals would turn to technology as a means of exploiting and stealing from others. To protect your data, money, and sensitive information from criminals, ensure that your cybersecurity partner is using only the most advanced and up-to-date standards and practices. Hammett Technologies is well-versed in cybersecurity and can guarantee your information’s safety from hackers and criminals.