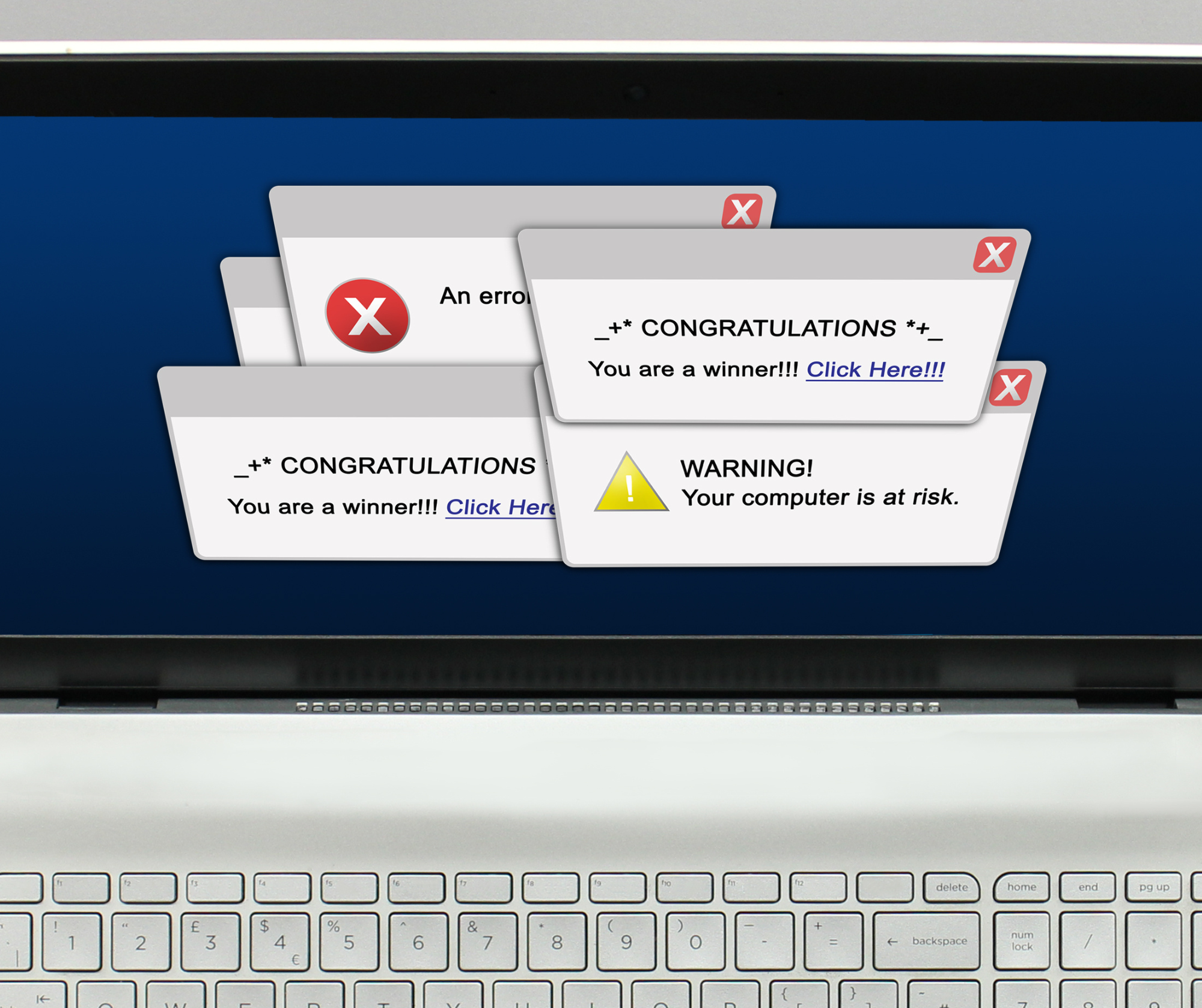
In the fast-paced world of business, where every click and download can have significant consequences, vigilance against cyber threats is paramount. Picture this: you’re diligently working away at your computer, focused on your tasks, when suddenly, a pop-up notification hijacks your screen. Your heart skips a beat as the ominous message declares that your PC is infected with a virus. Panic sets in, and the urge to click and resolve the issue becomes almost irresistible. But wait – before you take action, pause and consider: could this be a scareware tactic employed by hackers? Scareware is a malicious software tactic used by cybercriminals to trick users into downloading harmful software or divulging sensitive information. Often disguised as legitimate system alerts or notifications, these pop-ups are designed to incite fear and urgency, coercing unsuspecting users into clicking on them. Once clicked, the user may inadvertently install malware onto their device, compromising its security and potentially putting sensitive business data at risk. Small businesses, in particular, are vulnerable targets for such tactics. With limited resources dedicated to cybersecurity and employees wearing multiple hats, it’s easy for these deceptive pop-ups to slip through the cracks. However, awareness and education are powerful tools in the fight against cyber threats. So, what should you do if you encounter a suspicious pop-up claiming your computer is infected with a virus? First and foremost, resist the temptation to click on it. Regardless of how legitimate it may appear, clicking on the pop-up or any buttons within it could trigger a virus download. Instead, follow these steps to safeguard your system and protect your business: Remain Calm: Scareware preys on fear and urgency. Take a deep breath and resist the impulse to panic. Close the Browser: Safely close the browser window displaying the pop-up. Avoid clicking on the X, “Close,” or “Cancel” buttons within the pop-up itself, as this could activate the malware. Utilize Task Manager: If closing the browser proves challenging, access the Task Manager (Control + Alt + Delete on PC, Command + Option + Esc on Mac) to force quit the browser or application. Notify IT: Inform your IT department or designated personnel immediately. They can perform a thorough scan to ensure your computer remains secure and free from any potential threats. Educate Employees: Equip your employees with the knowledge and awareness to recognize and respond to scareware tactics. Regular cybersecurity training and updates are essential in fostering a culture of security within your organization. Implement Security Measures: Invest in robust cybersecurity measures, such as firewalls, antivirus software, and regular system updates, to fortify your defenses against cyber threats. By remaining vigilant and proactive, you can shield your business from the insidious dangers of scareware tactics. Remember, when it comes to cybersecurity, an ounce of prevention is worth a pound of cure. Stay informed, stay alert, and together, we can navigate the digital landscape safely and securely Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Data breaches and security vulnerabilities are rising, and not everyone is safe from emerging threats. The NSA and CISA report that many businesses need to follow the best practices. Discover some of the most common business security mistakes and how to stay safe in this helpful guide. Default Login Credentials Pose the Biggest Threat Nearly every application or business program executives use has standard default login credentials. Experts recommend only using these factory settings when you first set everything up. As soon as the programs are ready for use, it’s best to change the account’s credentials. This way, hackers have a lower chance of infiltrating your account. Creating strong passwords for all your accounts is essential to boosting network security, yet reports find that many IT professionals continue to use factory settings. Harmful Business Security Mistakes While using default credentials on applications and software is the most prevalent issue, CISA and the NSA note a few other security mistakes businesses regularly make. Experts recommend business owners make correcting these issues a top priority. Separating User and Admin Privileges Does your IT department grant anyone access to programs as an admin? Doing so can create big problems if they uncover malicious activity. It’s hard to pinpoint where the problem originates if every user has advanced privileges. Hackers can infiltrate the account and have unauthorized access to important data and information. Therefore, it’s critical to only give admin privileges when necessary and give all other users limited access to accounts. Poor Network Monitoring Experts point to a few ways companies need to monitor their networks sufficiently. These include failing to properly set up sensors to collect traffic and end-host logs. Stepping up in this area is essential to improve your business infrastructure and keep your network secure from threats. Importance of Cybersecurity Measures Some business leaders don’t realize they’re dropping the ball on security measures until too late. Falling victim to any cyber attack comes with significant problems, including: Loss of integrity and customer trust Data breaches Financial loss Business interruptions To avoid these costly consequences, technology professionals urge every business owner to emphasize the importance of cybersecurity in their workplace. Making IT staff regularly educate employees on the best practices sets up the entire organization for success. In addition, it’s vital to keep an eye out for emerging threats and take proactive measures. This may include downloading software updates after vulnerability exposure or adjusting security practices at the recommendation of agencies like CISA and the NSA. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Modern technology makes it much easier to operate a business. However, it can also cause major issues if you somehow lose access to critical data within your network. That’s why having a backup solution is important so all your data remains safe and readily accessible. Discover the crucial role of data backup and recovery in this helpful guide. Why Data Backup and Recovery Is Important Say a major storm passes through the area and your company’s building floods. The flood ruins all of your computer hardware, and you cannot access necessary data from another location. You can do nothing to stop natural disasters, but you can minimize the business impacts. Backing up all your data securely means you can resume business operations even if you suddenly need to work remotely. Data backup and recovery are also necessary to protect your business from human error. Say you accidentally delete an important file that is a key part of your latest project—having no backup copy available forces you to delay your project and hurts productivity. Performing frequent backups makes recovery times much faster so you can continue routine business operations. Your productivity won’t suffer if you can easily access an external drive or cloud server that contains your files and data. How Often Should You Perform Data Backups? Now that you understand the essential role of data backup and recovery, let’s discuss how often you need to back up your data. Technology experts urge every business leader to perform backups frequently. The longer you go without backing up your data, the longer your recovery time will be if the unexpected happens. Overcoming a natural disaster, accidental deletion, or system failure will be much simpler when you know you can easily access your data. For this reason, professionals recommend performing backups either daily or weekly. You can customize your schedule depending on how frequently your critical data changes. Data Backups Safeguard Your Business From Cyber Attacks One of the most important reasons you need to back up all sensitive data is to protect your business from malicious activity. Cybercriminals can perform data breaches that significantly affect companies and their clients. It’s much easier to mitigate the damage when you have a backup copy of files to deploy. Business leaders and their employees should habitually back up important data if a cyberattack occurs. Other measures that experts recommend include: Using strong encryption methods Regularly updating software programs Using multi-factor authentication to prevent hackers from gaining unauthorized access Teaching employees the best cybersecurity practices By protecting your data, you can avoid the dangers of cyberattacks. Protect Your Business Knowing the role of data backup and recovery can help you safeguard your business from physical and virtual threats. Counting on backup services can give you peace of mind regarding involuntary data loss. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
In the past, companies had to manage extensive computer networks on their own, purchasing servers and networking appliances and allocating physical space for data centers. However, the advent of cloud computing has transformed this landscape significantly. Today, companies can delegate most of their operations to the cloud, retaining only their LANs within their premises. The hybrid approach, where essential parts of the infrastructure remain on-site while other components migrate to the cloud, has gained popularity. Cloud service providers like AWS, Google Cloud, and Microsoft Azure have played a pivotal role in this shift, offering remarkable agility and flexibility. Cloud computing allows rapid scalability. If a company needs to double its data capacity, a simple adjustment in the subscription plan and some basic configurations can achieve this. Despite these advantages, effective management of cloud assets and cybersecurity remains crucial. Understanding Cloud Asset Management (CAM): When a company transitions its IT assets to cloud networks, these assets, such as hardware, software, and networking entities, become cloud assets. However, ensuring the seamless functioning and security of these cloud-hosted assets require expertise in Cloud Asset Management (CAM). CAM involves meticulous tracking of every aspect of a company’s cloud estate, encompassing maintenance, compliance, upgrading, and disposal of cloud assets. It’s imperative to be aware of the security features offered by cloud service providers and not overlook available security tools, as instances of underutilization have occurred. Challenges and Best Practices in CAM: Visibility into cloud assets presents a unique challenge. You can’t secure what you can’t see, making monitoring a critical practice. Networking monitoring tools become essential for ensuring that cloud providers adhere to Service Level Agreements (SLAs). Monitoring bandwidth and uptime guarantees the reliability of cloud assets, especially when numerous users depend on them simultaneously. Redundancy and automation are key allies in maintaining high uptime. Minimizing single points of failure, having data backups, and employing redundant servers enhance reliability. Automation not only reduces human error but also optimizes efficiency, particularly in repetitive cloud management tasks. A robust risk management plan is vital. Identify potential risks such as natural disasters, cyber attacks, and power outages. Develop specific procedures for each risk and ensure employees are trained accordingly. Security Assurance and Compliance: Critical security measures should be continuously monitored through actionable assessments. Automated systems can rectify vulnerabilities without human intervention, ensuring no security gaps are left unaddressed. Non-compliant cloud resources must be promptly shifted back into compliance, meeting the legal requirements of cloud technology. Incorporating my perspective, effective CAM not only provides security but also offers a strategic advantage. Understanding the nuances of cloud asset management empowers businesses to optimize their cloud usage, control costs, and ensure a seamless migration process. Moreover, it fosters a proactive approach, enabling companies to stay ahead of potential risks and leverage cloud resources to their fullest potential. In conclusion, CAM is pivotal for businesses embracing cloud computing. Remember, your cloud assets deserve the same attention as those behind your firewall. Stay vigilant, stay secure, and leverage the full potential of cloud services for your organization’s growth. Citation: Meena R., Cloud, Luminis India, October 16, 2023, https://luminisindia.com Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Hackers steal personal information from people who are vulnerable by making fake websites and sending phishing emails. If you fall for a phishing scam, private information like your credit card number could fall into the wrong hands. You can protect yourself from hackers in several ways, which is good news. Hackers can send phishing emails to business employees when they get their email addresses. They do this to get the workers to give out personal information. Most of the time, hackers want money and will try to get the person they are communicating with to send them their credit card number or information about their bank. If you fall for this scam, your sensitive information is at risk, and you need to move quickly to stop identity theft. How To Protect Yourself From Phishing Scams Phishing is one of the most common cyber-attacks impacting businesses. In a phishing email, the hacker will pretend to be a trusted person, like a bank representative or fellow employee, to trick the receiver into sending sensitive information. Use these tips to stay safe from phishing scams. Recognize the Signs of a Phishing Email Phishing emails are relatively easy to detect since most of them contain the same elements. Look out for any of the following items that are common in phishing emails: Unusual greetings Messages demanding urgent action Content featuring many typos and grammatical errors Strange senders asking you for login credentials or payment information Unknown attachments that use files like .zip, .scr, or .exe If you receive an email that raises your suspicion, don’t click on any links or open any attachments, as they may contain malware. Report the email to an IT professional who can mitigate the threat of further cyber attacks. Set Up Email Filters Your spam folder may automatically fill up with suspicious phishing emails, but savvy hackers are always looking to find ways to avoid the spam filter and get their emails to your inbox. You can set up additional email filters to protect you from scams, such as blocking the sender or flagging emails with strange attachments. Perform Regular Data Backups Protect your data by frequently backing it up to a hard drive or cloud service. If you access your business email on your phone, it’s also wise to back up your mobile data. This ensures that you can access data even if your device is compromised. Install Security Software Boost your protection against phishing scams by using security or antivirus software that guards against hackers and cyber security threats. Make sure that you program automatic software updates so the program actively prevents new threats that may occur. Use Multi-Factor Authentication One of the best ways to protect your accounts from phishing scams is by setting up multi-factor authentication for your email account and any sensitive accounts, like your login to your banking website. You’ll benefit from having additional security since your account will require another form of verification besides your password. This can be a one-time verification passcode, PIN, or correct answer to a security question. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
With hackers and cyber threats on the rise, it’s all your business can do to stay safe in today’s digital climate. Managed IT services are integral for protecting businesses from cyber-attacks. Learn more about what these third-party cloud services do and how they can keep your business safe from outside threats. What Are Managed IT Services? A managed IT service is a third-party resource that oversees your company’s information technology. While managed IT experts are readily available to address any issues with your network, their main goal is to avoid destructive threats. Outsourcing these concerns to an IT service provider ensures your business is in the best position against cyber-attacks. It also means you can save money by reducing the need for in-house IT staff. Your business can benefit from the two main types of service providers. Application Service Providers (ASPs) An ASP is responsible for delivering application software across a business network. This provider will oversee your specific applications, which is extremely helpful for your developers and vendors. Managed Service Providers (MSPs) An MSP can help small and medium-sized companies maintain a secure network. The managed IT services model’s main point is handling your daily IT operations. This option is great if your company wants to reduce your time devoted to fixing service interruptions or network issues. How Managed IT Services Prevent Cyber Threats ASPs and MSPs are excellent resources for different business models. However, the main benefit of these services is their protection against cyber-attacks. Your IT service provider will offer expert support and take action in the following areas. Advanced Network Security Measures Any outsourced IT service will do everything possible to protect your network from threats. This includes activating firewalls and antivirus software. The ultimate goal is to keep hackers from infiltrating and compromising your network. Your IT service provider will also keep your security software up to date to avoid dangerous hacks. You’ll have peace of mind that your business can run smoothly if your network is secure. Data Backup and Recovery Heightened security measures aren’t always enough. If a hacker obtains any sensitive data, you want to be able to access it during an unexpected breach. Managed IT services perform routine data backups so you can easily recover from a potential breach. Research shows that the average cost of a data breach is over $3.9 million. With a managed IT service backing up your data, you can minimize financial loss and maintain customer trust. Threat Management Managed IT services actively monitor potential cyber threats to your computer network. This will give you another layer of protection since an in-house IT team may not be as watchful. Any signs of a threat, such as a suspicious phishing email, will be flagged. From there, your experts will take proactive steps to minimize the threat and keep your business safe for the long term. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Our world is overflowing with data. By 2025, experts anticipate there will be 180 zettabytes of global data. That is an abundance of information. Managing all of this data, however, is a huge responsibility. It could cost a lot of money and even harm the environment if we do not. What Happens When We Waste Data All of this data storage requires energy. That energy is frequently derived from non-renewable sources. Data centers storing all this information are adding to carbon emissions. What’s more, there is not enough accountability for data management. Some businesses are wasting money storing unused and unwanted data. How Business Owners Feel the Pinch For business owners, especially in the IT sector, this is a big problem. Many spend a lot of money storing data they never use again. This waste is increasing as businesses collect more data. This puts a lot of pressure on IT leaders. 75% of them find managing excess data storage a significant stressor. Recognizing When We Waste Data To fix the issue, we first have to recognize the problem. Here are five signs your business might have data waste: If you are not adding the correct metadata. If you think the data has no purpose after you have used it once. If your team does not see value in the data. If there is poor communication between your teams. If your team is finding it hard to interpret the data. Tips for Better Data Management Avoiding data waste is about more than just having good tech. It is about changing how your team thinks about data. It starts with knowing what data you need and how to use it. Here are a few steps you can take: Equip your IT team with the right digital tools to manage data. Make a good plan for how you will handle data. Move your data into the cloud with the help of hyperscale providers. Invest in proper training and best practices. Don’t Drown in Data Managing data properly has become critical. You can make better decisions by understanding what your data is worth and the impact of storing it. Teach your team to understand data. Make a good plan for handling data. Give your IT team the tools they need. Instead of stressing about managing data, turn it into a chance to make your business run smoothly, save money, and protect the environment. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Your business website is your digital storefront. Its job is to attract visitors and convert them into customers. One thing that affects this process more than you think is how fast your pages load. This is known as page speed. Let’s explore why it’s so vital for your business. What Is Page Speed? Page speed is how quickly a page on your website loads onto a visitor’s device. Google, the most widely-used browser, uses a set of factors called Core Web Vitals to measure this: Largest Contentful Paint – how quickly the main content appears. First Input Delay – the time it takes for your site to respond to a user’s first action. Cumulative Layout Shift – how much your page layout moves while loading. Why Page Speed Matters Roughly 73% of mobile users have run into slow-loading websites. A website is considered slow if it takes more than 3 seconds to load. If your website is slow, you could be losing customers. Here’s why: User Experience: Most users want to start immediately. They will move on to another site if yours is too slow. Search Rankings: Google uses page speed to decide how high your site ranks in its search results. This is true for both mobile and desktop sites. Paid Search Traffic: If your website is slow, your ads may be shown less often and cost more. Mobile Traffic: Most people access the internet from mobile devices, and these websites are slower than desktop ones. What Slows Down Your Site Certain factors can slow down your website, such as: Images that aren’t optimized Large file sizes Inefficient web hosting Complex themes and designs Embedded media from other sites Heavy use of widgets Boosting Your Website’s Speed Luckily, there are ways to make your website load faster. Here are a few essentials: Switch to faster hosting: A faster web host can load your site quicker. It can make a big difference, especially if your host is slow or overcrowded. Choose a simple, SEO-optimized theme: Less complexity means faster load times. Themes with clean code and minimal design elements can significantly improve your site’s speed. A Content Delivery Network (CDN): A CDN will help load your site faster. A content delivery network stores copies of your site at different locations and allows users to access it from the nearest server. Minify and externalize CSS, JavaScript, and HTML: Minifying involves removing unnecessary characters in your site’s code, reducing its size, and increasing its speed. Compress and reduce files and images: Again, smaller is faster. Using compression tools, you can reduce the file size of images and other resources without affecting their quality. Enable lazy loading for images: This means images load only when needed, only some at a time. Speed Is Game-Changing for Business The loading speed of your company website can be a game-changer for your business. It affects how users experience your site, your rank in search results, and your ads’ performance. Focusing on speed isn’t optional if you want a successful business website. It’s essential. Don’t let slow load times hold you back. If you invest in website loading speed, your business growth also increases. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter

In the fight against phishing, Microsoft is one of the industry leaders. Its latest feature, launched in Windows 11 version 22H2, has a design that protects system credentials. The new feature will alert you if you paste your Windows password into a document or website. Impact on Business Owners This measure, part of the Windows 11 Enhanced Phishing Protection, helps businesses safeguard their credentials. You’ll receive a warning if an attempt is made to paste system passwords. By warning you of potential threats, it serves as an added layer of security for your business. Navigating the New Feature When you use the new feature, a window will appear if a Windows password is pasted into a website. It warns you about the risks of reusing passwords. It also suggests changing your local Windows account password and provides a link to the settings for an easy change. Potential Limitations Note that this feature might not work with third-party applications like Notepad2 and Notepad++. Moreover, the warning won’t trigger if you’re using Windows Hello, Microsoft’s password-less login feature. For this alert system to work, you’ll need to use a password to log into Windows, store it in the system memory, and reference it against pasted text. Ensuring Optimal Usage This feature is a significant stride toward more secure business operations. Here are a few tips to further optimize your system: Keep your system up-to-date. This will help you get the latest security features. Teach your team the risks of pasting system passwords into sites or documents. Encourage unique passwords for different accounts. Use multi-factor authentication when you can. This adds more security. Change passwords regularly. This reduces the risk of unauthorized access. Watch for strange activity or unusual login attempts. Make regular backups. This keeps your data safe. Use a password management tool. These tools can generate and store complex passwords. Embrace the Change for Enhanced Security Windows 11’s anti-phishing measure is a welcome addition to business security. This proactive approach from Microsoft is a vital step toward a safer business operation. By staying updated, utilizing this new feature, and adopting cybersecurity practices, you can provide your business with robust protection against online threats. Embrace the change and ensure a secure future for your business. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter

You may believe software updates are only intended to resolve bugs or add new features, but they have far more benefits for your business. They improve the compatibility and performance of your computer systems and, most importantly, strengthen your defenses against cyber threats. How Do Updates Help Your Business? Keeping your software up to date does a lot for your business: Increased efficiency. Updates can add new tools or improve old features, helping you and your team complete tasks faster. Enhanced collaboration. Cloud-based tools and other software help your team work together easier. Improved mobility. Mobile devices improve with each update, letting you stay productive wherever you are. Streamlined operations. Some updates add automation, which can do repetitive tasks for you, giving you more time for more important tasks. On the other side, outdated software can expose your business to significant risks: Data theft. If your software is old, cyber criminals might find a way in and steal your data. Operational interruptions. Outdated software can cause your system to crash or slow down, which can mess up your work. Higher costs. Keeping old software working can cost a lot of money over time due to technical problems or loss from data theft. How to Stay Ahead with Software Updates Regularly updating your software and operating system protects your business against hackers. Software updates often include patches that seal security loopholes, making it harder for cyber criminals to access your systems. Here’s what you can do to stay updated: Set up automatic updates. Check regularly for software updates if auto updates are not available. Educate your team about the importance of installing updates promptly. Make a schedule for checking and installing updates. Updates: The Secret Ingredient for a Successful Business Software updates are not just enhancements to your apps. They are a big part of making your business operations better and safer. By getting software updates as soon as they are available, you help your business run smoother and provide a safer place for work. Remember, an updated system is the first step in protecting your business from cyber threats and keeping it on its path to growth. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter