In today’s digital age, our personal data is more vulnerable than ever before. From financial information to health records, our sensitive data is constantly at risk of falling into the wrong hands. That’s why recent actions by the Biden administration to safeguard Americans’ personal data from “countries of concern” are so significant. President Biden’s executive order, issued last February 28, 2024, highlights the importance of protecting our most personal and sensitive information. This includes genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of personally identifiable information. So, what exactly does this mean for you and your data security? Firstly, it’s crucial to understand which countries have been identified as “countries of concern.” These include China, Russia, Iran, North Korea, Cuba, and Venezuela. These nations pose potential threats to our data security, whether through state-sponsored cyberattacks or other means. The executive order tasks the Department of Justice with implementing measures to prevent Americans’ personal data from being transferred to these countries. This includes working with other government agencies such as the Department of Homeland Security, the Departments of Health and Human Services, Defense, and Veterans Affairs, to ensure that federal contracts do not inadvertently aid in the transfer of sensitive health data. Additionally, the Committee for the Assessment of Foreign Participation in the United States Telecommunications Services Sector will review submarine cable licenses with a focus on potential threats to sensitive personal data. But what does this mean for businesses and individuals? For businesses, it’s a reminder of the importance of robust data protection measures. Companies must ensure that they are compliant with regulations and take proactive steps to secure sensitive information. This may involve implementing encryption methods, secure storage solutions, and continuous monitoring for potential threats. For individuals, it highlights the need to be vigilant about who has access to our personal data. We should be mindful of the privacy policies of the services we use and take steps to minimize the collection and sharing of our sensitive information whenever possible. Ultimately, President Biden’s executive order serves as a wake-up call to the importance of data security in an increasingly interconnected world. By taking proactive steps to protect our personal data, we can help safeguard our privacy and prevent it from falling into the wrong hands. Remember, your data is valuable – so let’s work together to keep it safe. Stay informed, stay vigilant, and stay secure. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
A new phishing campaign is making the rounds in an attempt for hackers to obtain sensitive information from vulnerable users. This campaign, first uncovered by tech researchers at Checkpoint, targets the popular cloud storage platform Dropbox. Learn more about the cybersecurity threat and how you can stay safe. Dangers of Phishing Hackers create ways to trick users into giving out their personal information, such as with deceptive emails or links to fake websites. They use messaging that claims a user needs to act urgently and provide sensitive data, such as credit card numbers or banking information. Once the hackers have this data, they can do with it as they please and wreak havoc on unsuspecting people. The dangers of phishing extend to business owners, their employees, and beyond. Victims must deal with the following issues: Financial loss or identity theft Violation of safety Lack of trust online How the Dropbox Phishing Campaign Works This clever campaign has several parts to it. Let’s review how hackers execute their plans step-by-step. Hackers Host a Document on Dropbox The plan begins with unknown bad actors creating a Dropbox account. They host a benign document that looks like a file from OneDrive and send phishing emails to users. Dropbox users will see a button that says “view document.” If they click, it leads them to malicious links. Hackers can implement the next phase after users end up on this site. Distribution Phase A key part of this Dropbox phishing campaign is getting users to a malicious site to harvest their credentials. Once someone ends up on this page, their information is given to cybercriminals who can use it against them. If you fall for the first part of the plan and have hackers stealing your credentials, it can be challenging to feel secure online again. Why This Attack Is Hard to Recognize Checkpoint reports that thousands of users have fallen victim to this attack. It’s particularly challenging to avoid since hackers use Dropbox’s system to share files and notify other users via email. Since the email comes from a reputable source, hackers can bypass any email scam filters or other protective measures you set up. This ultimately makes you more likely to open malicious links. The best way to keep your information safe from bad actors is to always be on guard. Refrain from assuming every email you receive is secure; report it immediately if something seems a little off. Experts recommend that business owners take the time to educate their employees on safe practices and report any suspicious email to an IT professional. Protect Your Business from Threats Every phishing campaign is different, but the threat remains the same. Keep your business safe from hackers by always staying alert and tracking widespread online campaigns. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
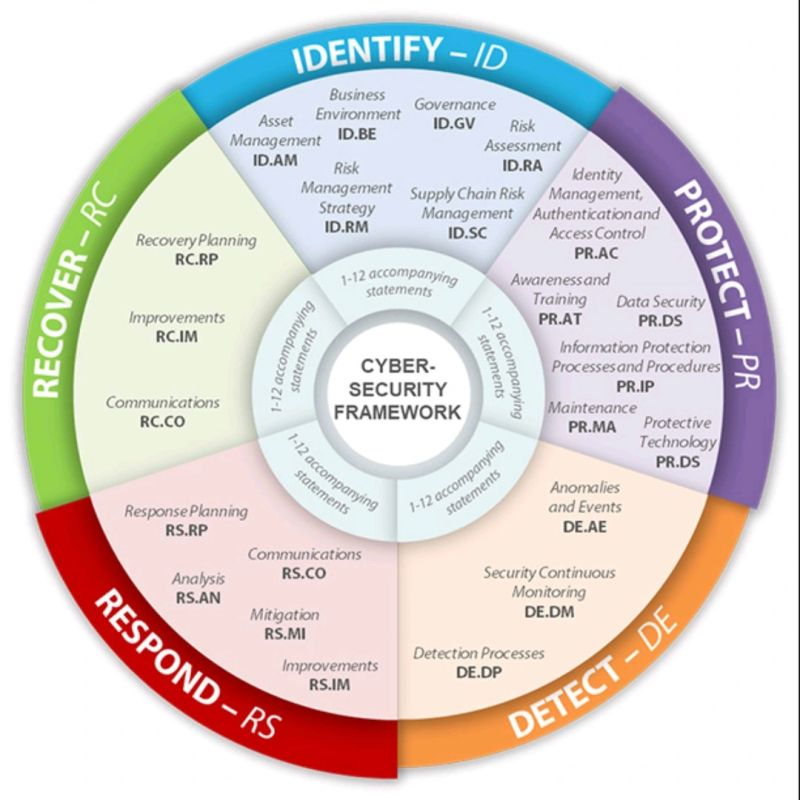
The NIST Cybersecurity Framework (CSF) stands as a cornerstone in the ongoing battle to secure our digital landscape. In today’s interconnected and data-centric world, safeguarding sensitive information and shielding organizations from cyber threats is paramount. At its core, the NIST CSF offers a comprehensive and adaptable approach to managing cybersecurity risks. It provides essential principles, best practices, and guidelines that empower organizations of all sizes and sectors to safeguard critical assets and bolster their overall cybersecurity readiness. Let’s delve into the framework’s fundamental components: 1️⃣ Identify: This initial stage revolves around recognizing an organization’s most valuable assets, such as customer data, intellectual property, and financial records. By understanding what needs protection, organizations can strategically prioritize their security efforts. 2️⃣ Protect: In this phase, implementing safeguards, preventive measures, and security controls is crucial. Activities like access control, employee awareness training, and encryption are key components, helping mitigate potential risks and vulnerabilities effectively. 3️⃣ Detect: Given the ever-evolving nature of cyber threats, it’s vital to establish mechanisms for promptly identifying and detecting potential incidents. Investments in advanced monitoring systems, boundary protection, and intrusion detection tools empower organizations to respond swiftly and effectively. 4️⃣ Respond: In the unfortunate event of an incident, having an organized and well-defined response plan is critical. This stage involves establishing communication protocols, incident reporting guidelines, and threat mitigation strategies to minimize damages and reduce downtime. 5️⃣ Recover: Following an incident, the focus shifts to restoring an organization’s systems, data, and processes to normalcy. Incorporating recovery strategies, backups, and continuous monitoring aids in bouncing back stronger and gleaning valuable insights from the experience. By embracing the NIST Cybersecurity Framework, organizations can: ✅ Foster Common Language: The framework enables the creation of a shared vocabulary around cybersecurity, fostering better collaboration between IT departments and executives. ✅ Assess and Improve: Organizations can assess their current security posture, identifying areas for enhancement and improvement. ✅ Enhance Communication: Clear communication of security efforts to clients, partners, and stakeholders builds trust and credibility. ✅ Strategic Alignment: The framework helps organizations prioritize resources, focus investments, and align cybersecurity initiatives with overall business objectives. However, it’s essential to recognize that cybersecurity is not a one-time event. Regular updates, reviews, and continuous improvement are imperative to stay ahead of emerging threats and maintain a robust security posture. Stay vigilant, stay updated, and stay secure. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
You check your inbox daily for important emails that help move your business operations forward. But what happens if you’re the target of a distributed spam distraction attack? This common cyber threat floods your inbox with thousands of emails that contain different spam messages. Read on to learn how to fight distributed spam distraction threats and go about your daily routine with greater peace of mind. What Is Distributed Spam Distraction? Distributed spam distraction is an online attack that hackers use to take over your email account. You’ll get tens of thousands of spam emails in a short time. The content of these messages is safe, unlike phishing emails that lead to viruses or the dark web. Your personal information is the main thing that is at risk here. If you start getting strange messages from people you don’t know, someone has hacked into your email account. The tactic of filling your inbox with spam makes it harder for you to see valid emails containing personal information. How To Fight Distributed Spam Distraction Distributed spam distraction is one of the most challenging cyber-attacks to deal with. It requires a multifaceted approach that involves the following tactics. Use Advanced Email Filters Your email already has a spam folder, but when it comes to a distributed spam distraction attack, hackers know how to get around it. Instead, the spam messages will go to your main email, making it hard to find important messages. The problem with this attack is that each email will come from a different sender, so you can’t just block them to stop getting spam. Instead, you should use advanced spam filters with machine-learning algorithms to find trends in spam emails. These filters become more accurate as they adapt and learn new techniques with every message in your inbox. Implement advanced filters throughout your organization to protect your employees from distributed spam distraction, phishing emails, and other cybersecurity threats. Cautiously Share Your Email Be wary of any site that requests your email information. If it doesn’t seem like a safe or reliable source, keep your email address private. Make sure that all of your workers know and follow the best security practices. For example, they shouldn’t open emails from people they don’t know or click on suspicious links or attachments. The following are some practical steps you can take to protect yourself from threats: Regularly update your passwords Set up text or email alerts whenever there’s an online purchase in your name Enable multi-factor authentication for extra security Update your security software Your business can stop distributed spam distraction and other cyber-attacks by updating its security software. If you don’t do this, you leave yourself open to attacks, which could lead to serious security problems and financial loss. Keep your security software updated to give yourself the best chance to fight hackers. Explore a wealth of information on our website https://www.hammett-tech.com/our-blog/ Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter
Running a business involves keeping your devices and digital assets secure. Fresh concerns have emerged with the recent discovery of two significant vulnerabilities in Apple’s software. These vulnerabilities were exploited in Apple devices with software older than iOS 15.7. Operation Triangulation and iMessage Attacks An operation called “Operation Triangulation” has led to the discovery of the flaws. Here, the iMessage app was the entry point for hackers. The harmful code they used could get into a device’s memory. It could execute commands, track the device, and collect data. The party behind the campaign is still unknown. Prompt Patches and Updates Apple quickly acted, releasing updates across iOS, iPadOS, macOS, watchOS, and Safari. These patches fixed the exploited vulnerabilities, including the two from Operation Triangulation. The two significant vulnerabilities are: CVE-2023-32434: This flaw at the kernel level can let a harmful app execute its code. CVE-2023-32435: This problem in WebKit could let unauthorized code run when handling specific web content. Along with these, Apple introduced a third zero-day patch for CVE-2023-32439. Like the WebKit flaw, this could let unauthorized code run when processing harmful web content. These patches are for devices from iPhone 8 onwards, all iPad Pro models, and the seventh-generation iPod touch. Defending Your Business: Practical Steps to Take So how can you shield your business from such threats? Here are four clear steps: Patch Installation. Act swiftly and install the latest patches from Apple. This is the critical first step to secure your devices. Antivirus Software. Use good antivirus software. It can scan, detect, and isolate threats to your device’s security. Automatic Updates. Turn on automatic updates. This will make sure your devices have the latest defenses as soon as they’re out. Cybersecurity Training for Employees. Your team can act as the first line of defense. Train them on how to recognize and avoid potential threats. Steering Clear of Cyberthreats These recent issues with Apple software stress the need for strong cybersecurity measures. But with the timely patches from Apple, there’s a way forward. You can keep your devices safe by staying updated and using strong antivirus software. You should also educate your team about cybersecurity. And safer devices translate to a more secure business. Visit our Socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter https://www.hammett-tech.com/apples-latest-ios-16-5-1-updates-security-flaws/
Government website services are seen as sources people can trust. However, threat actors use this trust for their harmful purposes. Scammers recently used official websites to advertise their hacking services. This situation shows why businesses should be on the lookout and take more robust computer security measures to avoid being affected by this type of risk. Hackers Use Flaws to Spread SEO Spam Scammers found weaknesses in US government websites and used them to upload advertisements for their hacking services. A federal agency and several universities were also affected. The ads were disguised as PDFs and offered hacking services for sale. There were links to websites showing different hacked social media accounts. They also provided services for fake followers and video game cheating. The ads were selling “easy and safe” hacking solutions that had no hidden goals. The people whose accounts were hacked even had names and images on some of the websites. Based on the PDF file dates, those ads have likely been there for some time. According to experts, the hackers have used open-source software, which can be used to create popups that make sure website visitors are real people. Due to security flaws, the SEO PDF ads surfaced on official websites. It seems like the hacking services advertised were made up as part of a click fraud campaign to get users’ money. While this complex attack went undetected for a while, it could have been worse. Instead of trying to sell scam services, the criminals could have uploaded infected links or content to the PDFs. It could have led to a massive data breach and other permanent consequences. For that reason, businesses should be aware of website weaknesses that can host SEO spam. A Call for Businesses to Prevent Security Problems Cybercriminals take advantage of any flaws. Businesses need to be aware of possible weaknesses, fix them, and use strong security measures. To build a solid defense, businesses must train their staff members to avoid these threats. Because scammers and hackers can affect their customers and clients, taking the necessary measures against them is vital. Read more blogs on: www.hammett-tech.com Visit or socials! https://www.facebook.com/HammettTech http://www.linkedin.com/companies/hammett-technologies Hammett Technologies (@HammettTech) / Twitter https://www.hammett-tech.com/scammers-use-government-websites-to-advertise-hacking-services/
Imagine putting money into an ad plan and having a tech issue cause costs to skyrocket. This issue hit many businesses when Meta Platforms, the owner of Facebook and Instagram, faced a large glitch. The unexpected surprise On April 23, 2023, a tech issue caused problems for businesses using Facebook for ads. This glitch forced companies to spend more money than planned. Though the glitch affected many, the impact was not evenly distributed. Big businesses that spend about $200,000 per month have a direct link to Meta and personal account reps. But smaller advertisers do not get the same luxury. Reimbursements Amid Controversy To rectify the situation, Meta began issuing refunds. This initiative provided some comfort, but it came with its share of skepticism. Some say the distribution of reimbursements appeared imbalanced. Reports hint at favoritism, suggesting advertisers with stronger connections with Meta received refunds readily. However, Meta maintains that refunds are determined case-by-case based on the unique circumstances of each issue. The Struggle of Small Advertisers The heart of the controversy lies with smaller businesses, many of whom felt the effects of the glitch profoundly. These businesses spend a lot on Meta’s platforms but lack the same support as the bigger ones. Some received refunds beginning on May 12, 2023. But the process has been slow for many, causing considerable anxiety. In response to the backlash, Meta promised to address the technical problem swiftly. Meta is focusing on improving the automated systems that originally caused the delivery mishaps. What can you do? As business owners, you should always keep an eye on your ad spending, especially on social media platforms. Remember that vigilance is key. If something looks off, reach out to customer service right away. Checking the return on your ad spending can also help you spot any issues faster. In the Middle of It All: Getting Trust Back As Meta continues its refund initiatives, the focus remains on regaining trust. It’s crucial that smaller businesses also receive the attention and support they need. By providing transparent processes and equitable treatment, Meta could do much more to rebuild trust with advertisers. This situation serves as a stark reminder: glitches can and do occur, and their effects can be far-reaching. If you spend time on these platforms, stay aware, be ready, and prepare your business for these issues.

Companies of all sizes have unparalleled access to information in today’s digital era. Data created by a business may give significant insights into its operations and performance, from customer interactions and sales numbers to staff efficiency and market trends. One of the most important ways companies can use technology to make smarter decisions is by utilizing data analytics. Businesses may obtain a greater understanding of their consumers, markets, and operations by gathering, organizing, and analyzing data and using this information to influence their decision-making process. There are various ways for businesses to employ technology for data analytics, including: Cloud-based data storage and analytics: Using cloud computing for data storage and analysis allows organizations constant access to their data from any device. With a variety of tools and services for gathering, storing, and analyzing data, cloud-based data storage and analytics systems, like Google Cloud or Amazon Web Services, make it simple for organizations to obtain insights and make wise decisions. Business intelligence (BI) software: BI software provides a variety of tools and functions for gathering, organizing, and analyzing data, as well as presenting it in an easily consumable style. BI software enables firms to identify patterns and anomalies in their data and make more informed decisions. Data visualization tools: Data visualization tools enable organizations to build interactive dashboards and reports that aid in making sense of large amounts of data. By displaying data in an easily consumable way, these tools assist businesses in identifying trends and patterns that may not be immediately apparent. By collecting, organizing, and analyzing data with the use of technology, businesses may get important insights that can guide their decisions. Whether you want to maximize your marketing efforts, enhance your sales process, or simplify your operations, data analytics can help you achieve your company’s goals.

Simplifying Cybersecurity: Microsoft’s Security Copilot AI Assistant Microsoft released a game-changing way to protect against cyberattacks. This AI-powered assistant, called Security Copilot, can find threats faster than ever. It could revolutionize how businesses keep their digital assets safe. Security Copilot uses OpenAI’s GPT-4. Microsoft’s “security-specific” AI model is also part of its structure. Security Copilot is designed to better summarize and make sense of threats than any tool before. How Security Copilot Does Its Job Some elements in Security Copilot come from other Microsoft security tools. With the help of AI, Security Copilot can give customized advice to any business. With Security Copilot, Microsoft aims to simplify identifying and organizing threat intelligence. As a result, analysts will be able to spot malicious behavior more quickly. Through a Chat GPT-like interface, users answer security questions. These interactions provide Security Copilot information to work on. It can be adjusted to fit each business environment and give custom advice. Benefits for Security Microsoft has made Security Copilot work well with cybersecurity teams. It gives defenders more ways to keep track of intelligence. The AI assistant helps them learn from the information they already have and compare the threats they face. This can lead to faster decision-making. This tool aids security teams in many ways: It catches what others may miss by correlating and summarizing attack data. It also prioritizes incidents and recommends the best course of action. This ensures timely remediation of diverse threats. Security Copilot can also learn and improve over time. This ensures that security teams stay up to date. They get the newest information about attackers, tactics, and procedures. Collaboration and Communication Features Security Copilot has features that make it easier for teams to work together. It can track what a user has done in the past to map out potential problems and create summaries. Colleagues can learn about the project and get up to speed. The system can also make presentation materials automatically. Then, teams can share information with people outside of their department. Use Security Copilot to Your Advantage You can use Security Copilot to improve your security. Consider these steps: Keep an eye on the latest advancements in cybersecurity tools like Security Copilot. Check your current security measures. Consider integrating Microsoft’s security ecosystem to enhance protection and threat response capabilities. Encourage training and education on cybersecurity best practices and their benefits. AI tools like Security Copilot help companies identify and address cyber threats. They provide vital threat information so that you can take the appropriate action. In addition, they automate tasks and enable wider collaboration between security teams. What does this mean to you as a business owner? With cybercrime increasing, focusing on security is essential more than ever. AI tools provide another layer of defense against attacks. In this regard, embracing AI tools is a wise decision for any business owner.
Bitdefender released its 2023 Cybersecurity Assessment report Wednesday, which surveyed more than 400 IT and security professionals located in the U.S., U.K., Germany, France, Italy and Spain. The report found that 42% of surveyed respondents said they were told to keep a breach confidential when they should have reported it, and nearly 30% said they had kept a breach confidential knowing it should have been reported. When it comes to U.S.-based organizations, those percentages only increased. The report also addressed the legal backlash of maintaining breach confidentiality. The primary threat concerns for surveyed respondents last year were software vulnerabilities and zero-day exploits, followed closely by phishing campaigns and supply chain attacks. Ransomware came in at No. 4. Bitdefender noted that patching software vulnerabilities in a timely manner is an ongoing problem that attackers increasingly leverage. Bitdefender released its 2023 Cybersecurity Assessment report Wednesday, which surveyed more than 400 IT and security professionals located in the U.S., U.K., Germany, France, Italy and Spain. The report found that 42% of surveyed respondents said they were told to keep a breach confidential when they should have reported it, and nearly 30% said they had kept a breach confidential knowing it should have been reported. When it comes to U.S.-based organizations, those percentages only increased. The report also addressed the legal backlash of maintaining breach confidentiality. The primary threat concerns for surveyed respondents last year were software vulnerabilities and zero-day exploits, followed closely by phishing campaigns and supply chain attacks. Ransomware came in at No. 4. Bitdefender noted that patching software vulnerabilities in a timely manner is an ongoing problem that attackers increasingly leverage. Bitdefender released its 2023 Cybersecurity Assessment report Wednesday, which surveyed more than 400 IT and security professionals located in the U.S., U.K., Germany, France, Italy and Spain. The report found that 42% of surveyed respondents said they were told to keep a breach confidential when they should have reported it, and nearly 30% said they had kept a breach confidential knowing it should have been reported. When it comes to U.S.-based organizations, those percentages only increased. The report also addressed the legal backlash of maintaining breach confidentiality. The primary threat concerns for surveyed respondents last year were software vulnerabilities and zero-day exploits, followed closely by phishing campaigns and supply chain attacks. Ransomware came in at No. 4. Bitdefender noted that patching software vulnerabilities in a timely manner is an ongoing problem that attackers increasingly leverage.