- All Posts
- Banners
- Business
- BUSINESSES WE TAKE CARE OF IN BALTIMORE & WASHINGTON
- Case Studies
- Charles
- Clients
- Cyber Security
- Design
- Development
- Information Technology News & Information
- Reports
- Services
- Startup
- Tech Tips
- Technology
- Uncategorized
- Video Library

With a plethora of tools available to protect our data, one of the most accessible options is likely already at your fingertips: Incognito mode. Incognito mode, also known as private browsing or privacy mode, is a feature present in most web browsers that enables users to browse the internet without…

With cyber threats on the rise, relying solely on passwords for protection is akin to leaving the front door of your house unlocked in a high-crime neighborhood. This is where two-factor authentication (2FA) steps in as a game-changer, adding an extra layer of security to thwart malicious attempts and safeguard…

One often overlooked aspect of safeguarding sensitive data and networks is the separation of personal and work devices. Mixing personal web surfing and social media with company devices can expose businesses to significant risks, including data breaches and cyberattacks. Why Should You Keep Personal and Work Devices Separate? Security Risks:…
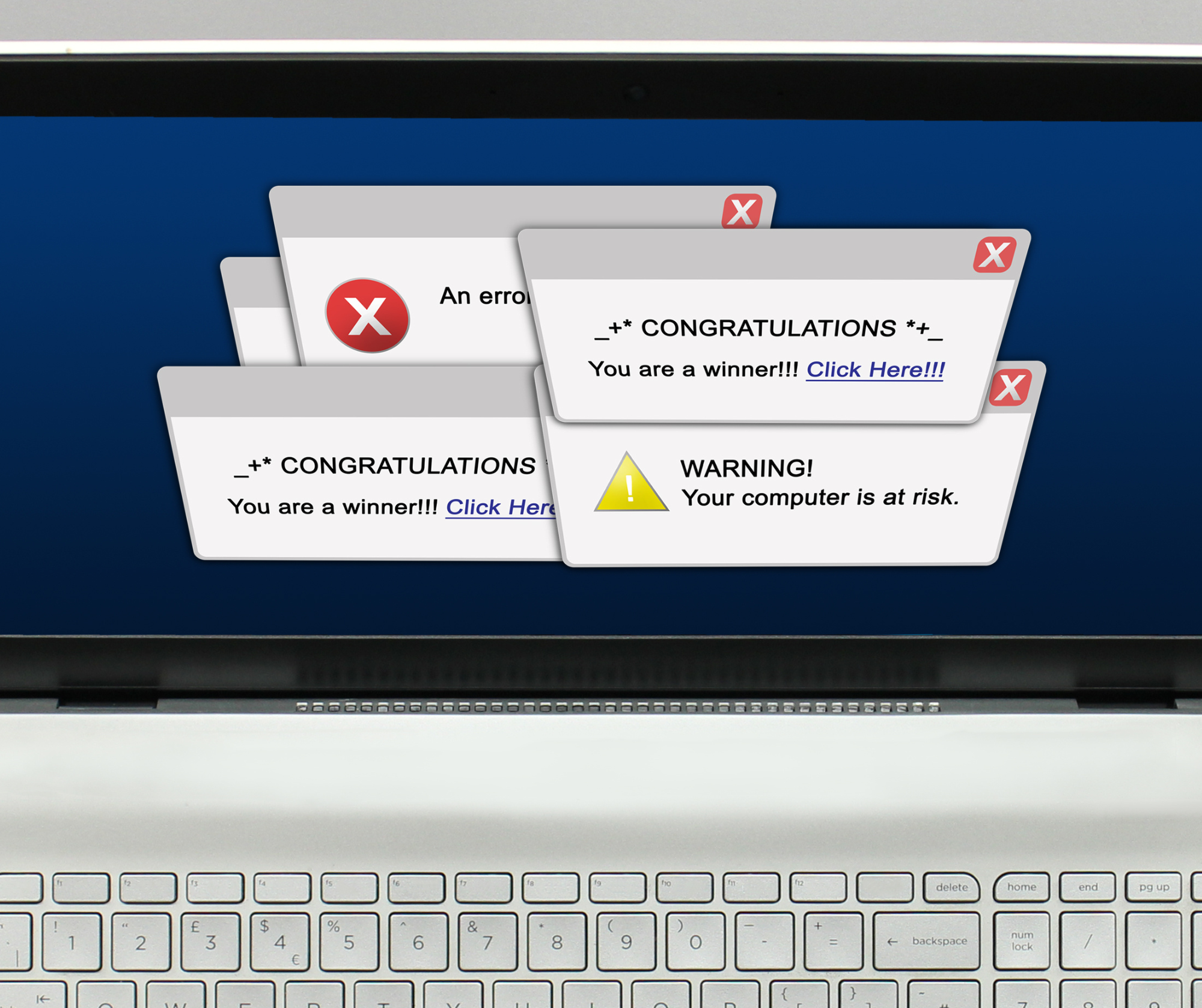
In the fast-paced world of business, where every click and download can have significant consequences, vigilance against cyber threats is paramount. Picture this: you’re diligently working away at your computer, focused on your tasks, when suddenly, a pop-up notification hijacks your screen. Your heart skips a beat as the ominous…

In an era where technology continues to revolutionize the healthcare landscape, the importance of robust cybersecurity measures cannot be overstated. As healthcare organizations embrace digital transformation, they become more susceptible to cyber threats, making it imperative to fortify their defenses. The healthcare sector has become a prime target for cyberattacks…

Data holds paramount importance for businesses of all sizes. Small business owners may assume that in-depth analytics are exclusive to large corporations. However, it’s essential to recognize that small businesses can not only obtain but also safeguard big data, especially in the realm of cybersecurity. SMB owners can benefit significantly from…

The ability of your team to exchange ideas, collaborate, and access relevant information can significantly impact productivity, creativity, and overall success. However, ensuring smooth information flow comes with its own set of challenges, and it’s essential to strike the right balance between open communication and safeguarding against plagiarism. We understand…

In our digitally-driven era, where our personal and professional lives are intricately entwined with technology, the significance of safeguarding our data cannot be overstated. Enter the realm of data backups—a crucial practice that, while offering a plethora of advantages, is not without its challenges and potential pitfalls. The Positive: A…

What Secrets Might Your I.T. Company Be Hiding? In the ever-evolving landscape of technology, businesses often rely on Information Technology (I.T.) companies to navigate the complexities of their digital infrastructure. While these partnerships can be immensely beneficial, it’s crucial to ensure that your I.T. service provider doesn’t inadvertently trap your…

In the rapidly changing realm of cybersecurity, keeping pace is not merely an option but a vital imperative. As cyber threats persistently evolve, organizations are seeking inventive strategies to fortify their security measures. Among these forward-thinking solutions, the fusion of virtual desktops for an elevated Zero Trust maturity stands out.…
